Hey Rebels, in an era of hackers and scammers one can’t be too careful with one’s online presence. To this end, we’ll be going over some Internet safety tips which will allow you to browse the web without any worries. In this post, we will cover the following
- Why we protect our online identity
- What an IP is and how to secure it
- VPN, 2FA and other protective practices
- Other threats to watch out for
Part 1: Securing your online identity
In today’s world, we interact with networked devices via the Internet every single day allowing us to communicate with one another, play games, learn and so much more. While the internet has given us significant and obvious comforts it also comes with a bunch of less obvious hazards. In this section, we’ll go over some of the well known hazards such as doxing and phishing, and how to protect yourself from it by staying anonymous online via a Virtual Private Network (VPN).
Doxing refers to any act which allows the attacker to gain unauthorized or non-consensual access to the victim’s personal information such as their real name, address, photo(s) etc. Attackers typically seek to use this information to blackmail and/or threaten the victim. Although it is extremely unlikely that this will happen to you, it’s good to take adequate precautions.
To understand how to protect yourself against doxing it important to know how data is transferred via a network like the internet. When any device joins a network (e.g. the Internet), it is assigned a unique Internet Protocol address (IP address or simply IP as shown in the picture below). To communicate with another device, your device searches for the recipients IP and it sends/receives information from it. IP addresses on the internet are assigned by your Internet Service Provider (ISP) and they depend on your geographic location.
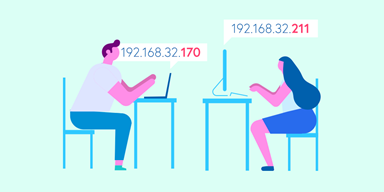
In the wrong hands, IP addresses can be used doxx or launch Denial of Service (DoS) attacks by spam pinging an IP address. Such attacks involve multiple bots flooding an IP with a massive number of requests in a very short amount of time that causes the targeted device to fail which typically results in a loss of internet connection. Therefore, it is vital to keep your real IP address safe.
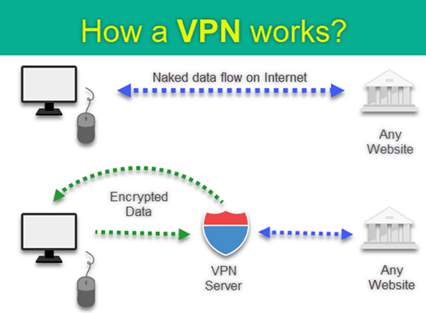
This can be achieved by means of a Virtual Private Network (VPN). A VPN reroutes all your internet data through a remote server as shown in the above figure. This allows your device to trick websites into thinking that the VPNs IP address is your IP address, thereby allowing you to keep your real IP safe. VPNs also encrypt the data between your device and the remote VPN server for added security. Some great free VPN options include hide.me, ProtonVPN and betternet. I highly recommend using a VPN while accessing Club Penguin Private Servers such as CPR and CPArmies.
Part 2: Safe Internet Browsing practices
In this section, we’ll go over some safe browsing practices which you can use while you’re online to stay completely protected. First, let’s go over some safe browsing habits that one should always try to follow.
- Be careful about what you share online
We need to be mindful of the nature of the information we share online and the people we share it with. Do not share information that can allow others to identify your personal information. Moreover, all files contain hidden information in them known as metadata. For photos, this can be in the form of the location at which the photo was taken, the make of the camera, the name of the person who took the photo and so on. People with malicious intent can extract metadata from a file sent by you to doxx and blackmail. Fortunately, many file sharing services including Discord have a built-in functionality that strips all files (like videos, images and audio clips) of their metadata, thereby, ensuring your privacy and protection.
- Do not click on unfamiliar links and don’t download unfamiliar software
Seemingly benign links can be designed to redirect you to dangerous webpages. These are known as Phishing scams. These webpages might contain malware, IP grabbers and scams. IP grabbers are designed to collect the IP address of the user with the intention of getting their location, which in turn can be used to doxx and blackmail. Attackers can also launch Distributed Denial of Service (DDoS) attacks on grabbed IPs and make it impossible for the victim to access the internet. If you feel that you’re being DDoSed contact your ISP as soon as possible and request them to change your IP address.
Even in the case of familiar links, it pays to double check the link before entering any sensitive information. Attackers can easily spoof links and make them seem legitimate as shown in the following picture
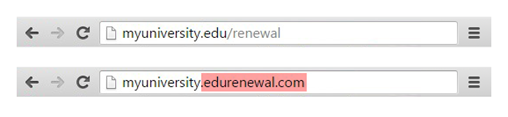
Do not download software from unknown sources since it can infect your pc with malware and potentially spy on you. It is a good practice to run scans on files that you download to make sure that you remain safe. The easiest way to prevent phishing is to not respond to the attacker. If you’re presented with an online offer that is too good to be true, then in all probability, it isn’t true and it is a phishing scam. In the event your username or password is lost by means of a phishing attack, be sure to immediately change it and turn on 2FA for the affected account, thereby preventing the attacker from accessing your account.
Now, let’s look at some steps that can enhance your safety through the magic of cryptographic encryption!
- Setup a strong password on all your online accounts
Setting up a long password (15 characters or more) with a mixture of upper and lower case letters, numbers, and special characters such as @, ! and ? make it a lot harder for hackers to use brute force to guess your password and access your account as illustrated in the picture shown below. The picture is for illustrative purposes only, we do not recommend the use of any password that spells out or looks like “password”.
 Ensure that your password is not the same as your username and that it is free of your personal information and commonly used words. Try to keep a unique password for each account you have. This will ensure that if one account is breached, the others stay safe. Feel free to checkout password storing services like lastpass that can autogenerate and store strong and unique passwords for each of your accounts.
Ensure that your password is not the same as your username and that it is free of your personal information and commonly used words. Try to keep a unique password for each account you have. This will ensure that if one account is breached, the others stay safe. Feel free to checkout password storing services like lastpass that can autogenerate and store strong and unique passwords for each of your accounts.
- Turn on Two Factor Authentication (2FA)
2FA is an extra layer of security used to make sure that people trying to gain access to an online account are who they say they are. First, a user will enter their username and a password. Then, instead of immediately gaining access, they will be required to provide another piece of information. This second factor typically comes from a device in your possession like a smartphone or tablet as shown in the image below.
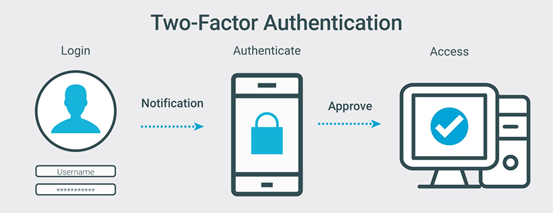
Some of the common 2FA apps include Google Authenticator, Authy and Duo. Once set up, if you attempt to log on to your account, you will be asked to provide a code. The code will be available on your smartphone or tablet for a limited amount of time. 2FA can be linked to one device alone (i.e. one tablet or phone that you have), therefore, it prevents unauthorized access to your account even if someone manages to get the rest of your login credentials (i.e. username and password). Many online accounts including Discord, WordPress, Google, Facebook and Snapchat provide 2FA and we highly recommend that you turn on 2FA on all your online accounts
- Be cautious while visiting unencrypted websites
Websites that don’t use an encrypted connection will have an address that always starts with http://. Any information you send and receive from such websites is vulnerable and visible to hackers. If a website uses encryption, any information sent and received from the site will be encoded using a numerical cipher. Such websites will also have an address starting with https:// and will commonly feature a lock symbol right next to it. The following graphic illustrates the difference between an unencrypted and an encrypted connection.
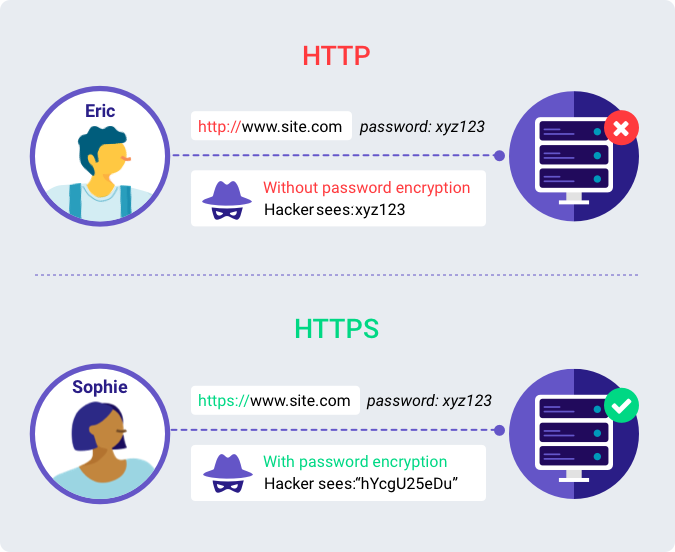
In the case of websites with encryption, the encoded data (both sent and received) cannot be deciphered without a decoding key. This key is unique and private to you and the website and it cannot be obtained by a hacker through brute force without the use of sophisticated supercomputers. Therefore, sites which use encryption (https://) can guarantee the safety of your data. However, sites without encryption provide no such guarantee and it is good practice to avoid sending personal and sensitive information on unencrypted sites (http://) without the use of a VPN.
Part 3: Protect yourself from Malware
When it comes to cybersecurity, the single most important thing is to ensure that the device you use to connect to the internet is safe and free from malware. Malware refers to any computer program that’s designed to cause extensive damage to files and systems and/or to gain unauthorized access to private networks. Malware is typically delivered in the form of a link or file and requires the user to click on the link or open the file to execute the malware.
Protection from malware can be easily achieved by means of an antivirus. An antivirus (AV) is a computer program that constantly runs in the background and runs scans for malware signatures in your computer’s files. There are many free AVs that provide excellent protection against most forms of malware. For example, I’ve used Avira AntiVir Free and remained free of malware for the last 12 years. Once you’ve installed an AV on your computer, it’s very important to enable automatic updates of your computer’s operating system (OS) and the AV. This will ensure that your computer receives critical security patches as and when they’re released by the manufacturer of the OS and the AV, and it will make it a lot harder for malware to infect your PC. Running periodic automatic scans on your device is a sure shot way of keeping your device safe from malware.
Lastly, be sure to speak up and educate others regarding online safety. If you’re unsure regarding anything on the web, please do not hesitate to ask. RPF HCOM and mods are here to help you out. If you’re the victim of a cybercrime, do not hesitate to speak out. Be sure to educate your friends and encourage them to follow safe browsing practices.





yes
yes
Pingback: GS 101: Avoid Getting Phished » Rebel Federation - Gaming Community